Google Cloud Platform (GCP) uses service accounts to authorize applications or services. Azure Pipelines typically stores these credentials as Service Connection. However, a GCP Service connection is unavailable. Therefore we use Secure Files.
Secure Files
The Azure Pipelines Library provides Secure Files to store secrets without including them in source control. Files are project scope and permissions are controlled using roles. Just like service connections.
Remark Secure file usage history is not available. Use file permissions to ensure that your file is used by the appropriate teams and pipelines.
Add secure files to your project via Pipelines > Library > Secure Files.
Authenticate As Service Account
The following Azure Pipelines snippet uses a Secure file to configure the Google Cloud SDK credential.
steps:
- task: DownloadSecureFile@1
name: serviceAccount
inputs:
secureFile: 'azure-deployments-example.json'
- task: GoogleCloudSdkInstaller@0
inputs:
version: '291.0.0'
- task: GcloudRunner@0
inputs:
command: 'auth activate-service-account'
arguments: '--key-file $(serviceAccount.secureFilePath)'
displayName: 'gcloud auth activate-service-account'
The pipeline assumes that:
- Secure file ‘azure-deployments-example.json’ exists
- The google-cloud-sdk-tasks extension is installed
The Google Cloud SDK credential is configured by callinggcloud auth activate-service-accountwith a credential stored as Secure file. This causes allgcloudcommands to use the activated credential.
Discussion
Secure files can’t be updated. Rotating a secret thus requires you to recreate the file. In effect, all pipelines need to re-authorize with the Secure file-resource.
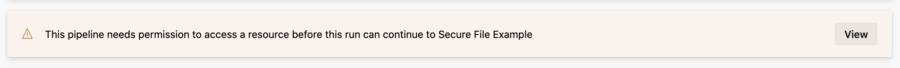
I’m fond of this re-authorization process. However, I do understand that it differs from Service Connections. Since Service Connections are unavailable, you could use Variable Groups. The variable group injects a secret pipeline variable containing the service account credential. Since Google Cloud SDK requires a file, the pipeline needs to write the secret variable to a file:
variables:
- group: azure-deployments-example
steps:
- task: Bash@3
inputs:
targetType: 'inline'
script: 'echo $(ServiceAccountKey) | base64 -d > _key.json'
- task: GoogleCloudSdkInstaller@0
inputs:
version: '291.0.0'
- task: GcloudRunner@0
inputs:
command: 'auth activate-service-account'
arguments: '--key-file _key.json'
displayName: 'gcloud auth activate-service-account'
This pipeline assumes a Variable group ‘azure-deployments-example’ and a base64 encoded variable ‘ServiceAccountKey’. The use of ServiceAccountKey is described by Google in Creating a CI/CD pipeline with Azure Pipelines and Cloud Run
Conclusion
Secure Files is a secret store suited for storing Google service account credentials. Combined with the Google Cloud SDK extension it’s easy to authenticate and act as your service account.






